Three Lines of Defense
How They Contribute to a More Effective AML/CFT Organization
📅 July 9, 2024
📅 July 9, 2024
“[I]n the context of AML/CFT [Anti-Money Laundering / Combating the Financing of Terrorism], the business units… are the first line of defence in charge of identifying, assessing and controlling the risks of their business… The second line of defence includes the chief officer in charge of AML/CFT, the compliance function but also human resources or technology. The third line of defence is ensured by the internal audit function.”
– Basel Committee on Banking Supervision, Guidelines on Sound Management of Risks Related to Money Laundering and Financing of Terrorism 2020
In this article, we will look at how the “three lines of defense” model, also called the “three lines” model, can be applied in financial institutions, keeping in mind that there are many variations based on the size of the institution and its preferred operating model.
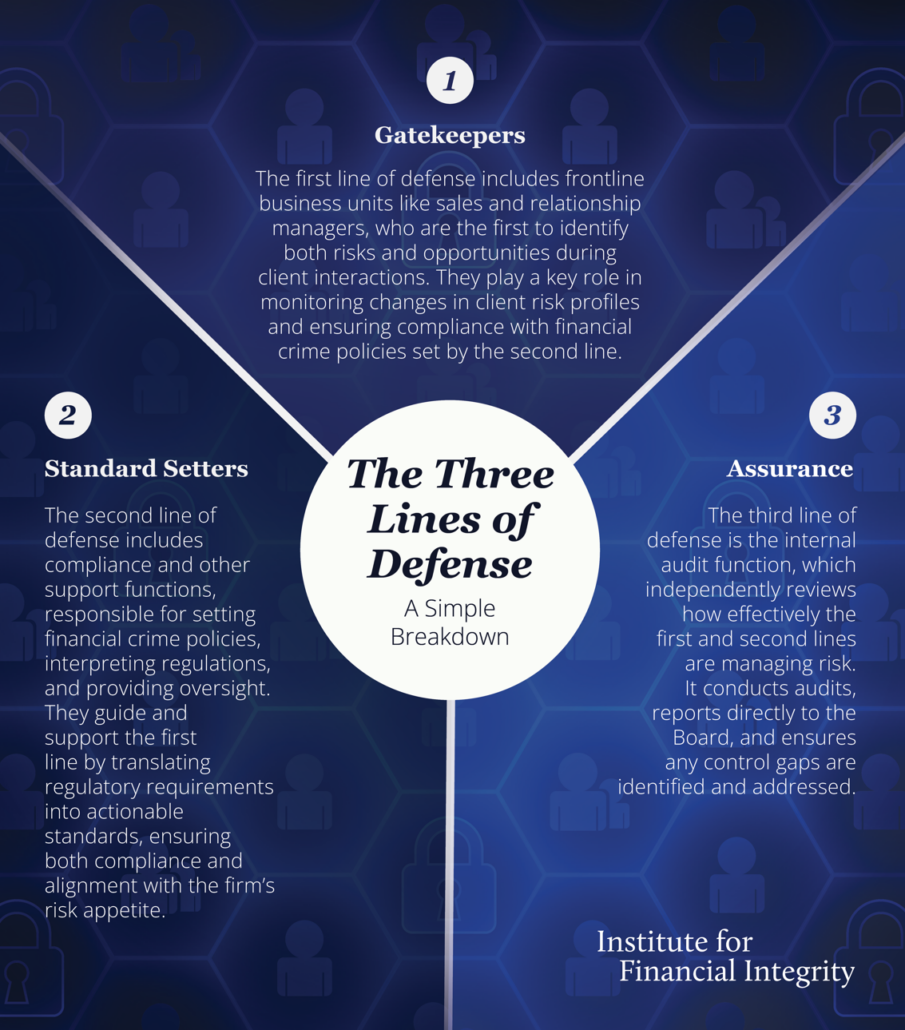
The First Line (1LOD)
The first lines of defense are the business units of a financial institution, including sales, relationship managers, traders, and sometimes client-facing support staff. These staff have the initial interactions with potential and current clients, which provides them with the first opportunity to identify risk factors – as well as potential business opportunities. These staff also engage throughout the client lifecycle, enabling them to identify changes that impact the risk profile of their clients.
Some examples of situations that may change a client’s risk profile include:
🚩 A client expands into new global markets which have higher financial crime risks than their existing markets, such as proximity to sanctioned countries;
🚩 A client introduces new products which are dual-use items subject to export controls, requiring additional levels of due diligence;
🚩 There are changes in corporate ownership or directors who may be politically exposed persons (PEPs).
First line staff are responsible for implementing and ensuring compliance with the financial crime risk management policies and standards set by the second line.
The second line of defense comprises the compliance function as well as other support functions such as technology and human resources.
The second line may also undertake broader responsibilities such as responding to regulatory proposals. Their experience of how compliance works within a financial institution gives them expert knowledge to make suggestions on how to achieve policy objectives, while ensuring the proposed measures can be implemented in practice.
The third line of defense is the internal audit function, which provides independent oversight of the design and effectiveness of the first and second line controls. Internal audit conducts regular reviews and reports its findings directly to the Board of Directors or a Board Committee.
The key advantage of the lines of defense model is that it provides segregation and prevents conflicts of interest between those setting standards and those applying them. For example, the Basel Committee states that, “to enable unbiased judgments and facilitate impartial advice to management, the chief AML/CFT officer should, for example, not have business line responsibilities.”
Looking at an example of what could occur if these responsibilities were combined, if a person was assigned sales targets to bring in new business as well as being responsible for setting compliance standards for new clients, there would be a conflict between their two objectives and a risk that one would be disproportionately prioritized over the other.
By providing segregation and independence, the first and second lines can work together in mutually complementary ways.
The three lines model has other benefits.
✔ It can support specialization in knowledge and skills, enabling depth and capability to be achieved.
✔ Training can be customized to be specific to the tasks of each team, making it more relevant and therefore more likely to be remembered.
✔ It can help avoid duplication where functions overlap.
However, the model also has limitations. For example, in new and emerging areas where in-demand skillsets are scarce and the evolution of products and markets requires new solutions, what adaptation need to be made to the lines of defense? View our recorded webinar,Mastering Compliance in Digital Assets through Multi-Tiered Defense Strategies to find out more.
The digital assets sector presents unique compliance challenges, including a complex and rapidly evolving regulatory landscape, misuse of digital assets in financial crime, and the need to adapt existing risk and compliance frameworks to include digital assets. As this industry continues to grow, with projections indicating substantial market expansion, staying ahead of compliance requirements and future challenges is crucial for financial institutions to safeguard their operations and reputation, while benefiting from the potential of this asset class.
Effective defense strategies are paramount to mitigating these risks and maintaining the highest standards of compliance. Led by industry experts, panelists will assess the integral roles of the first and second lines of defense in maintaining rigorous compliance frameworks and will dive into the future challenges that could redefine regulatory landscapes. Prepare to gain actionable insights and forward-looking strategies to elevate your compliance practices in the fast-evolving world of digital assets.











 Crypto Under the Microscope
Crypto Under the MicroscopeThis site uses cookies. By continuing to browse the site, you are agreeing to our use of cookies.
Accept settingsHide notification onlySettingsWe may request cookies to be set on your device. We use cookies to let us know when you visit our websites, how you interact with us, to enrich your user experience, and to customize your relationship with our website.
Click on the different category headings to find out more. You can also change some of your preferences. Note that blocking some types of cookies may impact your experience on our websites and the services we are able to offer.
These cookies are strictly necessary to provide you with services available through our website and to use some of its features.
Because these cookies are strictly necessary to deliver the website, refusing them will have impact how our site functions. You always can block or delete cookies by changing your browser settings and force blocking all cookies on this website. But this will always prompt you to accept/refuse cookies when revisiting our site.
We fully respect if you want to refuse cookies but to avoid asking you again and again kindly allow us to store a cookie for that. You are free to opt out any time or opt in for other cookies to get a better experience. If you refuse cookies we will remove all set cookies in our domain.
We provide you with a list of stored cookies on your computer in our domain so you can check what we stored. Due to security reasons we are not able to show or modify cookies from other domains. You can check these in your browser security settings.
These cookies collect information that is used either in aggregate form to help us understand how our website is being used or how effective our marketing campaigns are, or to help us customize our website and application for you in order to enhance your experience.
If you do not want that we track your visit to our site you can disable tracking in your browser here:
We also use different external services like Google Webfonts, Google Maps, and external Video providers. Since these providers may collect personal data like your IP address we allow you to block them here. Please be aware that this might heavily reduce the functionality and appearance of our site. Changes will take effect once you reload the page.
Google Webfont Settings:
Google Map Settings:
Google reCaptcha Settings:
Vimeo and Youtube video embeds:
You can read about our cookies and privacy settings in detail on our Privacy Policy Page.
Privacy Policy